Interactive Directory
& Digital Directory for Building

Discover the Interactive Directories & digital directories board and signage Kiosk by MetroClick

Searchable Tenant Directory
Search by company name or individual.
Time and Weather
Current temperature and forecast.
News Ticker
Displays the latest news headlines.
Financial
Dow, NASDAQ, S&P 500.
Announcements and Ad Space
Manage a slideshow of building news.
Display events
Host local and national ads.
DIGITAL BUILDING DIRECTORY software SOLUTION
The MetroClick digital directory solution allows the landlord to manage new and existing tenants, employees and advertising opportunities in real time without experiencing any of the added cost of a print-based solution. All of our clients have a dedicated Content Management System (CMS) that allows them to augment the directory and it’s on-screen content simply and effectively.
Interactive Directory Kiosk Signage for lobby
With MetroClick’s complete hardware lineup you can chose from a 22” to 84” large format touch screen monitor, large wall mounted monitor or our line of touch screen kiosks, to enhance your directory’s impact.
Take Advantage of Our Large Format Touch Screen Directory for malls
The MetroClick large touch directory allows for incorporating company logos, weather, news, transit information and more. With an interactive directory, you have unlimited listing capabilities for your building’s tenants and organizations.
More Information
Display Relevant Digital Information
A MetroClick digital directory instantly provides the most relevant information to anyone entering your building. Get in sync with the time, weather, and current events, with just a glance. When it’s time to leave, check out the directory’s transit schedule to catch live departure times.
MetroClick designs and develops touch screen directories in-house, in New York, NY.
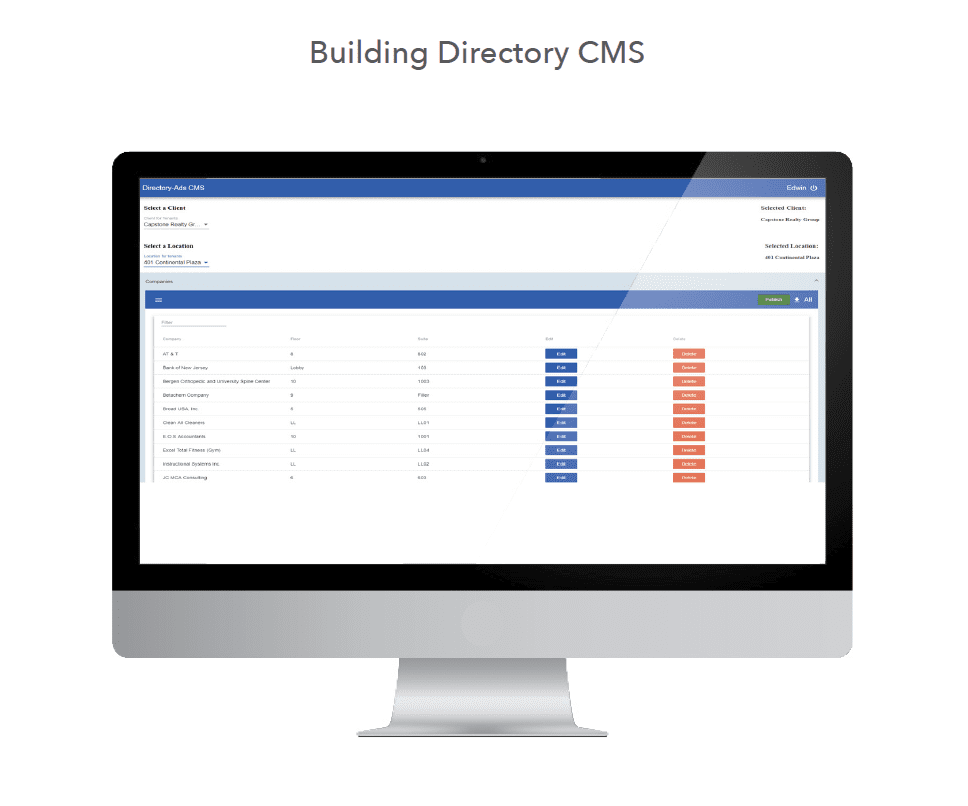
Custom Content Management System
Take complete control of your directories with a custom Content Management System to edit current tenant listings. Don’t be limited by print. When using an interactive directory, tenant listings can be updated in seconds!
A standard directory is printed and the signs are constantly changing. The cost to get signs printed can add up, and they are inconvenient to maintain. Managing tenants through our CMS is quick and easy. Best of all, updating listings can be done at no additional cost.
Our focus at MetroClick is to eliminate the hassle of traditional real estate directory products and provide a simple all-in-one solution to address all of the needs within a single system. The benefits of utilizing a single digital solution far outweigh the return and expense of traditional print signage solutions. From a cost, ROI and opportunity to monetize the digital solution, we feel that this is a great solution that benefits both the tenants and landlords in an effective solution that creates significant upside for revenue generation and tenant satisfaction.
The MetroClick digital directory solution allows the landlord to manage new and existing tenants, employees and advertising opportunities in real time without experiencing any of the added cost of a print-based solution. All of our clients have a dedicated Content Management System (CMS) that allows them to augment the directory and it’s on-screen content simply and effectively. Additionally, the MetroClick team is available as needed to aid any of our clients with issues, new concepts and on-site help to ensure a seamless and smooth process.
MetroClick’s aim is to be a one-stop-shop for any and all of your digital signage, interactive experience and custom solution needs within a single partner/vendor. We look forward to working with you to tailor a solution that is cost-effective, highly functional and aesthetically pleasing to meet all of your needs. For any additional questions, quotations or other needs please don’t hesitate to contact us directly. We are excited to assist you in bringing your digital directory solutions to the digital space and look forward to hearing from you.
Our Interactive Directory App is Loaded with Features:
- Custom Branding and Imaging
- Interactive Company Logos
- Train Times
- Building and Facility Information
- Building Announcements
- Time & Date
- Weather
- News Ticker
The MetroClick Interactive Digital Directory Displays Far More than Simple Text
Contact Us
for Solutions
Have questions? Interested in a quote or RFP? Contact us today and one of our specialists will follow up ASAP!
California
804 Anacapa Street
Santa Barbara, CA 93101
Florida
7630 NW 25th ST
Suite 2A
Miami, FL 33122
Metroclick Offices
T: 646-843-0888
New York
239 West 29th Street
Ground Floor
New York City, NY 10001